A Crypto Survival Guide: How to Immediately Improve the Security of your Wallet
Quick steps to step up your security given the increasing scams.
What do crypto and an old Windows have in common?
Both are a minefield.
Navigating the crypto ecosystem has become increasingly complex.
Every day scammers find new ways to circumvent security measures and attempt to take control of your assets. This is not even about naivety, a mere moment of distraction, and BOOM, your life savings are gone.
This can happen in so many ways:
Clicking a wrong link
Clicking a wrong Google ad
Joining an unofficial Discord group
Interacting with an imposter on Telegram
Accessing a malicious website
Perhaps a hacked friend sends you a seemingly innocuous Google Doc on something you working on…
Even the biggest NFTs projects are not immune: their Discord could get compromised and share malicious links, leading you into traps.
This is a major barrier to entry for new users.
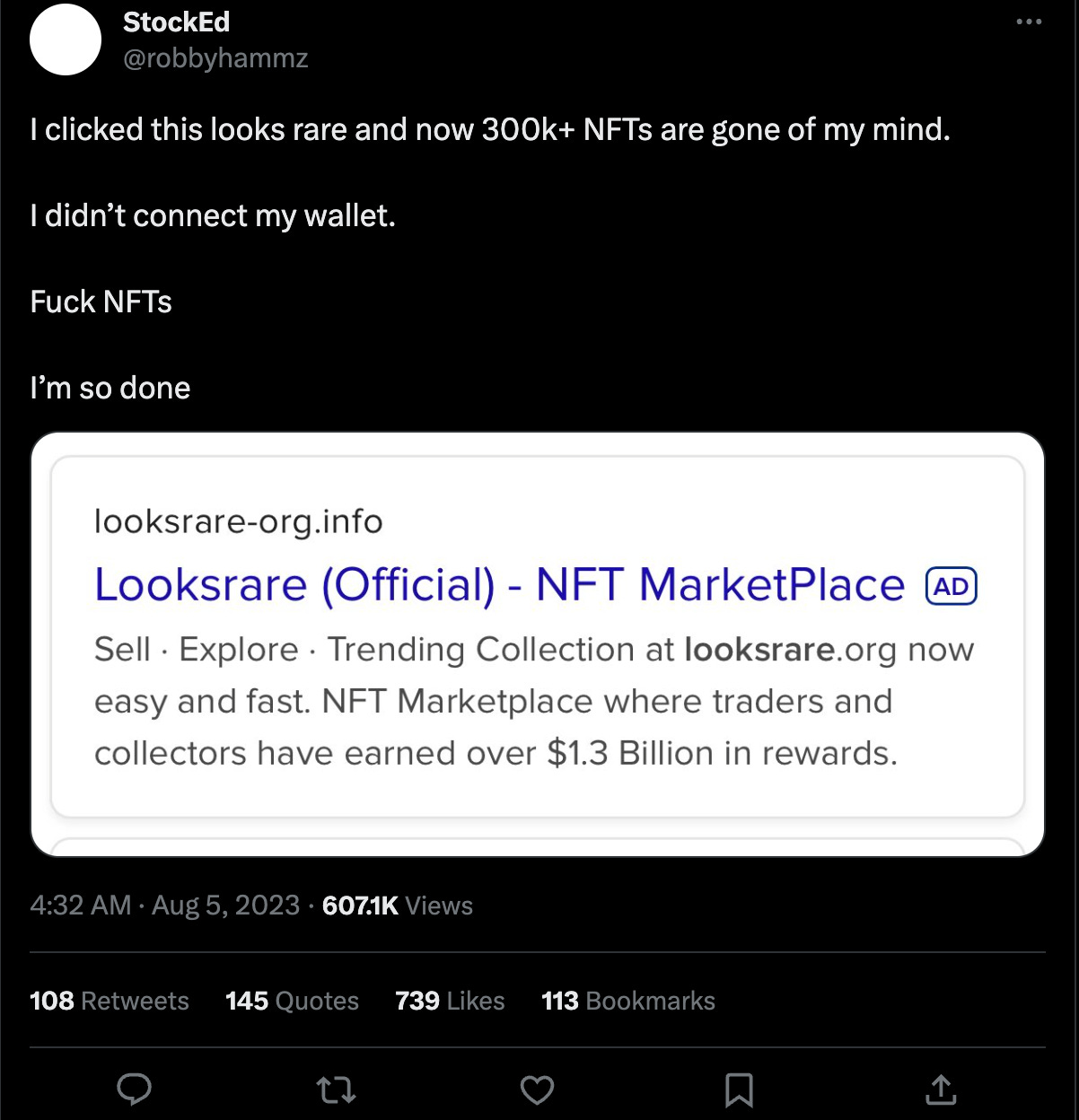
Imagine sharing with your friends interested in crypto that a simple misclick on a Google ad can cost someone 300k+ in NFTs.
Crypto is a tough sell.
It all started like this..
There are also several factors that have to be taken into consideration:
The majority of users overlook essential security practices
Scammers evolve more rapidly than security tools
Regrettably, tools like Metamask have been very slow to step up the security of their wallet, despite leading the market for years.
While scammers advance, our security often lags.
But the tools that can help us are out there, it’s just a matter of not being lazy and stepping up our security.
We always see scams as something we would never fall into.
Until we do.
So.. What can we do to protect ourselves?
Here are some steps we can take to step up our security:
Invest in a hardware cold wallet
Get rid of Metamask for Rabby
Install Wallet Security Extensions
Periodically revoke Contract Approvals
Before diving in, remember that your security level depends on your threat model and which adversary you are up against.
Get a Hardware Wallet
It’s astonishing how many degens store excessive amounts on software wallets like Metamask.
This effectively means that you are always 1-2 clicks away from losing it all.
A hardware wallet can cost anywhere between 90/400€, including the most complex ones.
If you are invested even a couple of thousands in crypto, getting one is a prudent move. Ledger isn’t your only option out there — lots of startups are crafting more privacy-focused hardware wallets, such as the Grid Lattice or the Bitlox Ultimate.
Hardware wallets add an extra level of protection as you need your physical wallet to confirm every transaction carried out.
But in itself, hardware wallets won’t save you from getting scammed.
They can though save you from impulse-clicking links, but if you link your wallet and approve a transaction, your funds are vulnerable.
Always check what are you signing.
This brings us back to the screenshot of the hack at the beginning of this article, where the victim claims that
Well, this is simply not true. One way or another, he did connect the wallet and confirmed and signed the transaction.
If you don’t connect your wallet they can’t steal your funds.
However, hardware wallets are not the holy grail of security.
It is important to add that not a single hardware cold wallet at the moment is fully Open-Sourced - not even Trezor, Ledger and the ones cited above. Also, if you go to their websites you can see that they are one of these companies does not consider the bug-bounty report "in scope" if you have physical access to the device
This is a worrisome aspect since Trezor ”serves as the basis for many hardware wallet clones out there, but it also has no physical security which is why there are numerous key recovery services you can reach out to for extraction if you own one”.
Companies like Trezor and Ledger have faced recent criticism:
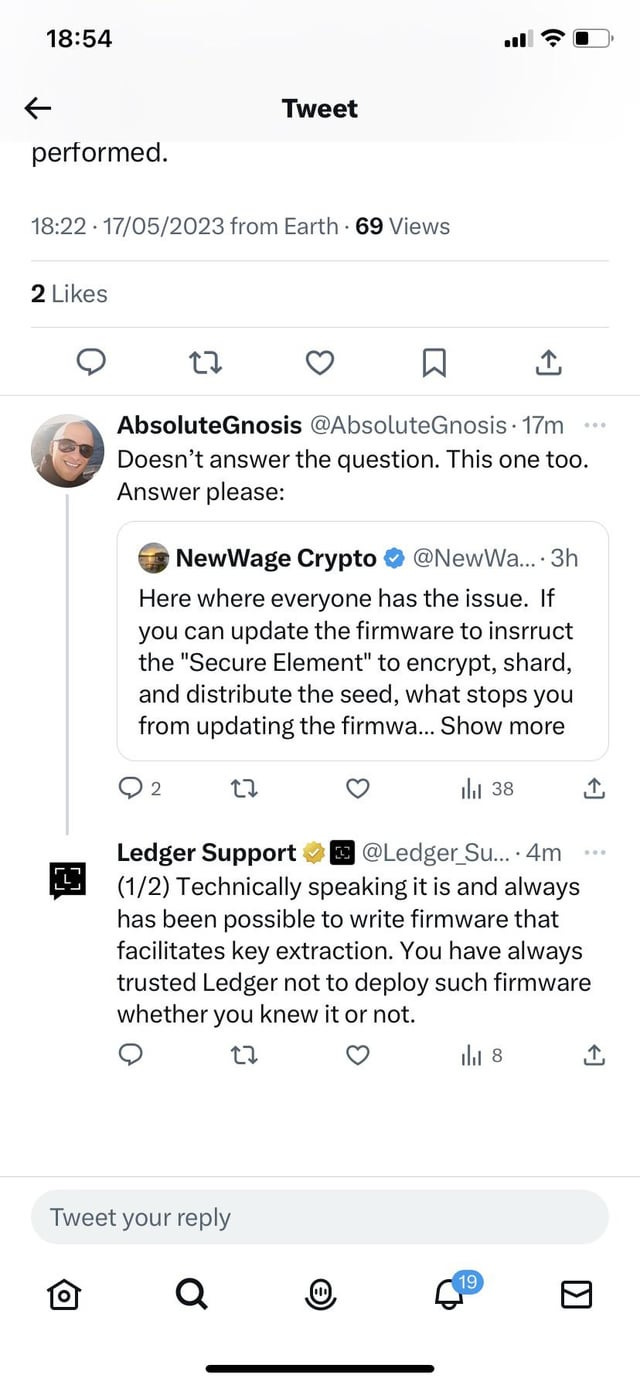
Ledger acknowledged its ability to extract a user's private key via a firmware upgrade.
This emerged after a user commented about the launch of their new product: Ledger Recovery.
On the other hand, a security company has shown that it is very well possible to physically hack into a Trezor wallet.
There’s also another video online with a user being able to recover funds by hacking a Trezor:
Some more articles on hacked hardware wallets:
As you may have understood - hardware wallets are not perfect.
If you decide to purchase a hardware wallet, always buy them directly from manufacturers.
Avoid Amazon or eBay since these devices might be tampered with.
Nonetheless getting a hardware wallet is an improvement.
What’s even more important is to organize wallets by function, and maintain separate COLD and HOT wallets.
This distinction is pretty straightforward: never use your cold wallet for casual work.
Be a degen on your hot wallet and safely send your funds over to your cold wallet.
Among the possible improvements to this OpSec, it would be nice, for instance, to include warnings and descriptions on the transaction you are signing, which brings us to the next point.
Ditch Metamask for Rabby
If you are still using Metamask, you either like being hacked or you haven’t checked Twitter for the last few years.
This is one of those “Game of Thrones” situations where everyone just keeps telling you to check it out!!!!
I eventually downloaded Rabby after a bit of peer pressure AND now I get it.
Why is everyone obsessed with Rabby?
Rabby is a wallet extension, developed by the Debank team.
While technically similar to Metamask, it is greatly improved with regard to:
UX
Security Warnings for Users
In-app Swaps
Multichain Portfolio Tracker
In-app Revoke
Our King monosarin here sums up some of the main differences:
By using its own RPCs Rabby does not share your information with third parties providers such as Infure - contrary to what Metamask does.
This also means that Rabby automatically switches across all supported networks, as well as having waaay fewer RPC issues - especially on new networks.
Rabby’s privacy policy is also better than Metamask:
But more importantly, Rabby brings about a couple of security-focused improvements:
You can revoke contracts directly in-wallet by simply clicking on approvals on the wallet homepage:
It then opens a page showing you all the contracts you have ever approved with your address, which you can also sort by token.
Similarly to Revoke Cash you can then select all of them and revoke permission.
Every time you connect to a new contract or have to sign a transaction Rabby gives you an explanation of what you are about to sign, as well as showing you a graphical warning to inform you of the related risks.
At the last moment, you may realize that the contract you are about to sign might be compromised, and might steal your funds.
Last minute save.
Every new wallet created on Rabby has a new seed phrase. On the other hand, every time you create a new account on Metamask it is derived from the same seed phrase as the others.
But surely Rabby itself is not enough to save you from everything.
Consider pairing it with a supportive browser extension.
Browser Extensions
Browser extensions won’t make you more secure. Their main purpose is to help you understand what you are signing and alert you of malicious transactions.
Here are a few of the most known ones:
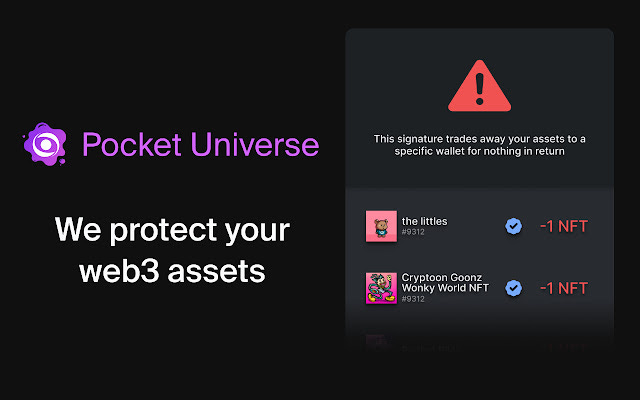
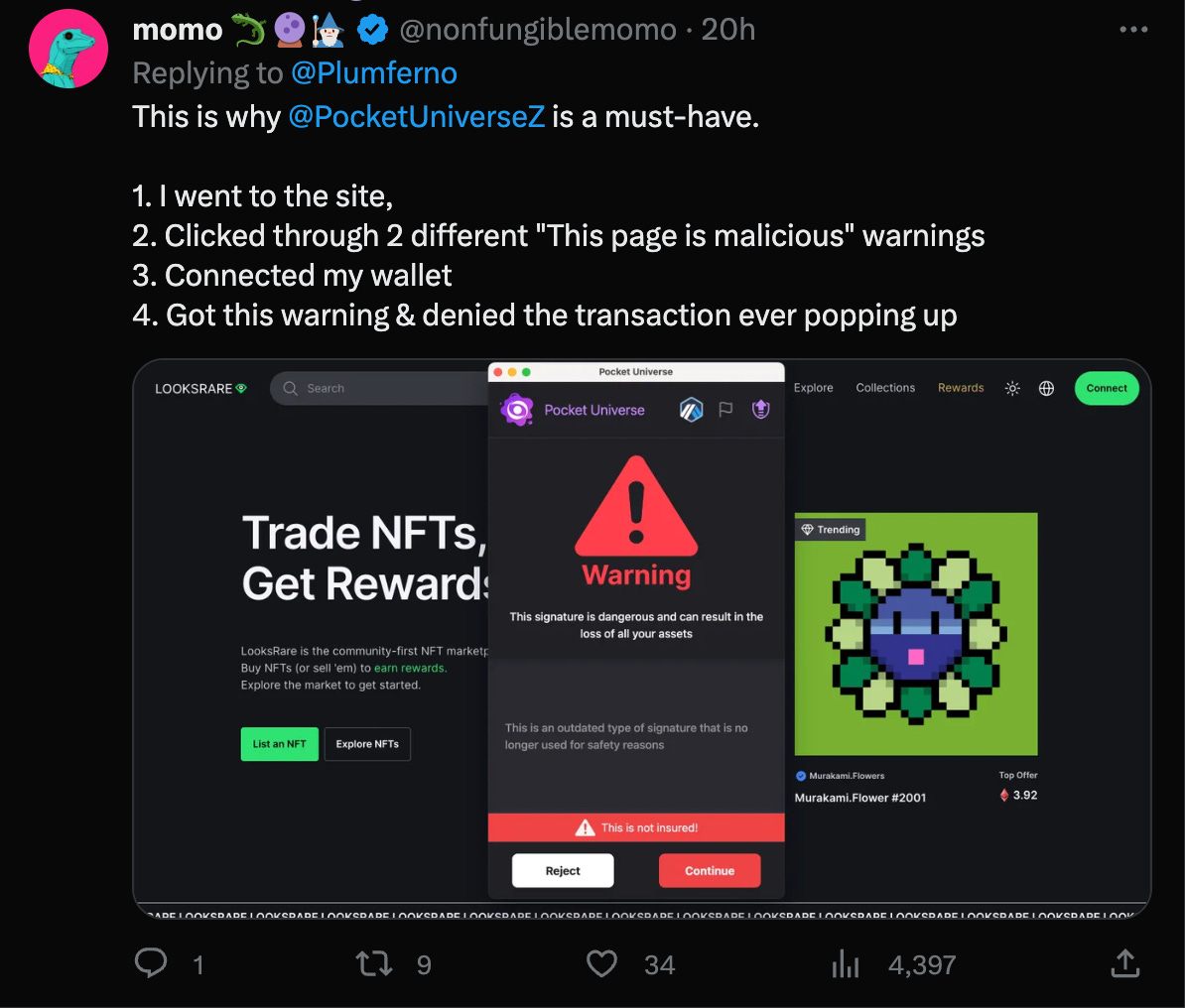
1. Pocket Universe
The differentiating element of Pocket Universe is that they simulate every transaction and signature and show you its outcome before sending it through your wallet.
What’s cool about Pocket Universe is that they also offer Insurance of up to $2000 on funds lost to scams that they don’t warn you about!
For more information on the insurance, you can refer to the Pocket Universe website.
2. PeckShield - Aegis Web3
PeckShield is a blockchain security company providing auditing and threat protection services, which also incubated Aegis, a security browser extension.
Among its services, AegisWeb3 can:
Block phishing sites
Check token contracts
Manage approvals
Report risks
Like Pocket Universe, AegisWeb3 also simulates transactions and displays the results to you.
3. RevokeCash
Revoke is the browser extension of the popular website allowing you to revoke smart contract permissions.
The main purpose of this extension is to pop up and inform you of the approval details every time you are about to sign an approval transaction.
This also works for NFTs - and is a useful addition that works as an additional warning.
Currently, the Revoke extension is available on Ethereum, Polygon, and Avalanche.
Which one should I use? Is there any difference?
I wouldn’t be picky here tbh - you can easily download all of them and use your favorite ones interchangeably.
Some might miss specific transactions, that others may instead be aware of.
Using more than one will provide maximum security coverage!
On the negative side of the Web3 browser extension, we have to mention the fact that as third parties dApps, they all require you to trust the developing team.
Sure, some of them come from teams like PeckShield, which is a known auditing company, but nonetheless installing a browser extension comes with third-party risks.
Installing an extension introduces new software to your browser—software that could potentially have security weaknesses (or be downright malicious). Third-party extensions might secretly include malware, or have security flaws that hackers can exploit.
Furthermore, the use of browser extensions also implies the fact that our data and personal information will be collected and disclosed.
For instance, these are the terms and conditions of Pocket Universe with regard to information disclosure:
Just like wallets, browser extensions also gather and share your data with third parties. As such, using them is not recommended for everyone.
However, if you have an active wallet that you use frequently to transact, then browser extensions may come in handy to increase warnings of malicious contracts.
Here’s a more extensive article with more examples of Web3 browser extensions:
https://medium.com/@wiimee/web3-browser-extensions-yay-or-nay-efa6cdb70983
Finally, regularly revoke all contracts.
This very easy practice is often overlooked and can go a long way to save your ass-ets.
You can do so within Rabby or on Revoke Cash.
Aside from the ones we have already mentioned, there are a couple of bonus measures you should be aware of.
Disposable Addresses
Ideally, you should never use any of your addresses more than once.
Every time you are getting a transaction you are supposed to create a new one, to preserve your privacy. While admittedly cumbersome, disposable addresses are gaining traction.
Airgap
Did you know that you can easily turn your phone into a cold wallet?
Airgap is an interesting solution whereby you download an app and you are able to use 2 phones one of which is not connected to the internet to create a cold wallet.
Wallet Scrutiny
As mentioned above, most wallets are not open-source - you can use some tools such as Wallet Scrutiny to verify whether a wallet is secure and open-source.
Using an encrypted email provider and never linking your phone number to crypto platforms are also two other best practices.
More best practices from Officer CIA:
I am by no means a security expert.
But that’s the beauty of it. You don’t really need to be.
There’s no barrier stopping you from stepping up your security literally right now.
But if you do want to learn more from an expert on the subject I highly recommend you take a look at Officer Cia Blog, which is the main source of some of the materials I used for this article:
https://officercia.mirror.xyz/
and his thread on the subject: